
HIPAA One® Privacy Breach Assessment Tool
- 10,000+ Assessments Performed
- 100% OCR Acceptance
- 3x YoY Efficiency Gains
Get a HIPAA One Demo
Trusted by 64,000+ Providers




















Streamline Your HIPAA Privacy and Breach Compliance
The HIPAA Privacy and Breach Notification Rules requires healthcare organizations, health plans, and business associates to have physical, administrative, and technical safeguards in place to protect the privacy of PHI.
That includes a mandatory risk assessment to identify and rectify compliance gaps.
To help organizations fulfill their obligations, our HIPAA Privacy and Breach Risk Assessment (PBRA) offering combines Intraprise Health’s highly rated privacy and security services with our industry leading HIPAA PBRA software, HIPAA One®.
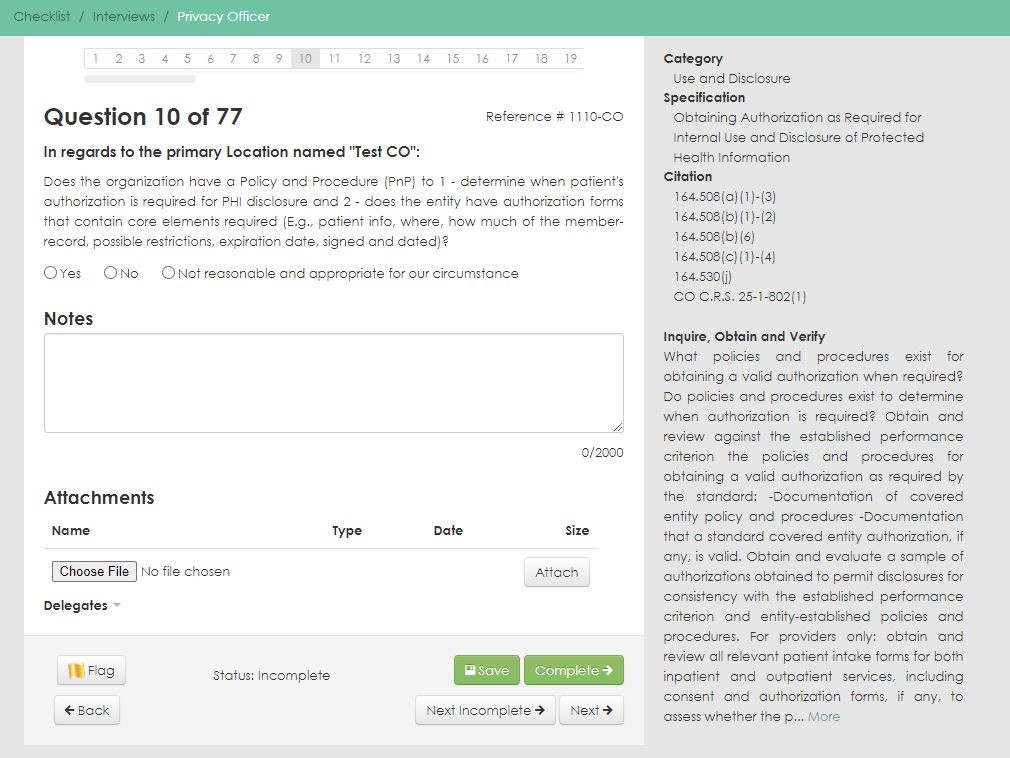
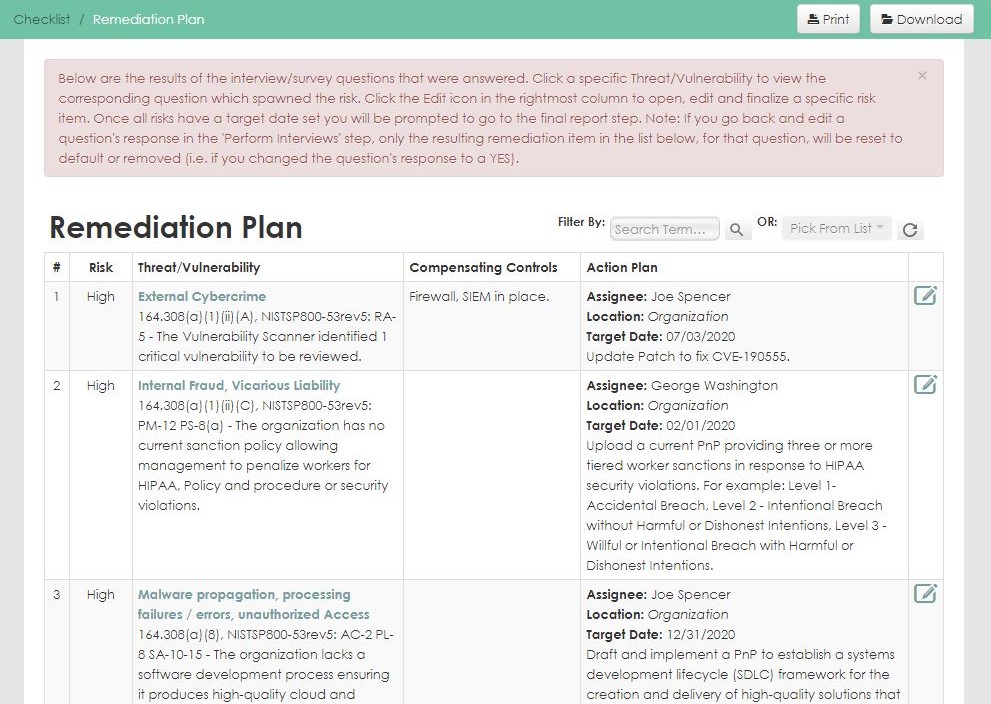
Gain the Confidence You Need
Regardless of your organization type, our comprehensive tool provides a guided approach to meeting the requirements of the HIPAA Privacy and Breach Notification Rules.
Based on NIST 800-series methodologies, the software covers the current OCR Audit Protocol, State specific regulations, 42 CFR Part 2 (SAMHSA) and maps to the NIST Privacy Framework.
Whether you are a healthcare organization, health plan, or business associate, we have options available to help you successfully complete your PBRA.
You can independently complete your PBRA using the HIPAA One® compliance software, or if you would like greater assistance, our Assessors can work with you in a collaborative approach to assess your current privacy and breach risk management program and help you identify and lower your risk.
Address the Four Factors of a HIPAA Breach Assessment
The HIPAA Breach Notification Rule outlines four factors of an effective breach assessment, and our tool comprehensively addresses all areas:
1. Assessing the nature and extent of PHI: Analyze the types of PHI involved in the security incident, such as demographic information, medical history, or financial data, and provide a complete overview of the potential impact and sensitivity of the compromised information.
2. Identifying unauthorized access or recipients: Identify any unauthorized individuals who may have accessed or received the PHI. Detect patterns, anomalies, and potential breaches involving external parties or internal personnel.
3. Determining the actual acquisition or viewing of PHI: Examine relevant data to determine whether the compromised PHI was acquired, viewed, or accessed by unauthorized individuals and provide insights into the extent of the breach to help you understand the full risk.
4. Assessing risk mitigation measures: Evaluate the effectiveness of existing security controls, safeguards, and mitigation measures implemented by your organization by identifying any gaps or weaknesses in the security posture and providing recommendations for strengthening security measures and reducing risk.
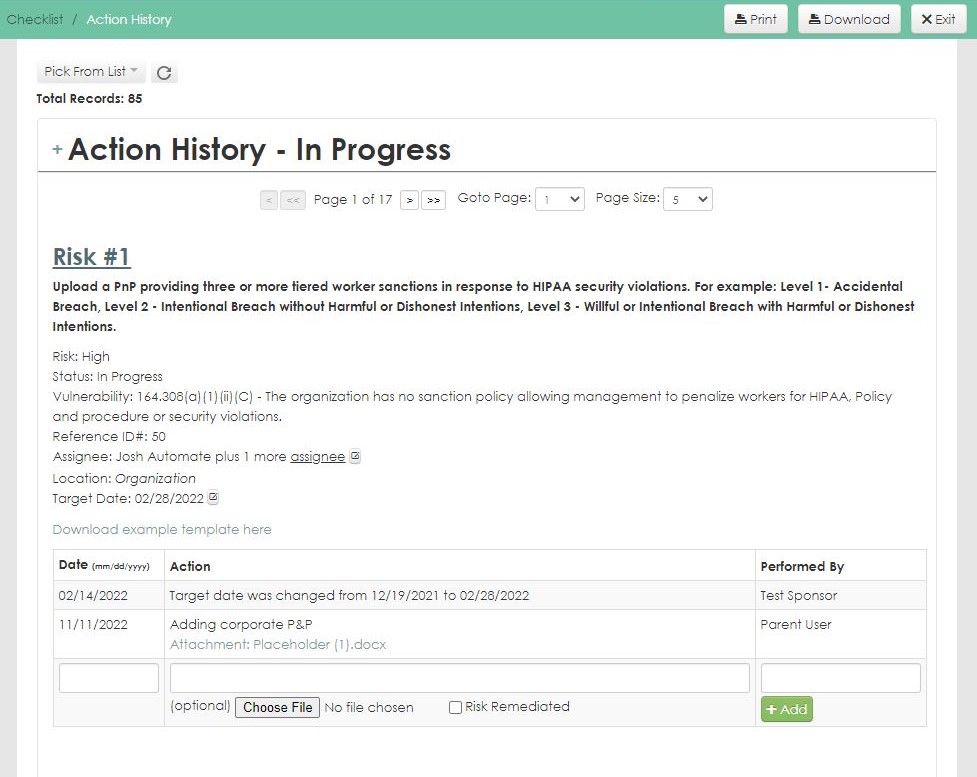
Everything You Need to Stay Compliant in One Tool
- Gap Analysis – step by step guidance on compliance
- Policy and procedure templates provided to help you correct deficiencies
- State Law database included in the assessment
- Up to date privacy regulations
Privacy & Breach Risk Assessment Engagement Types
Guided Assessment
Independently Conduct your Risk Assessment Utilizing HIPAA One
Our Guided PBRA Includes:
- System workflow guides you through the assessment
- Access to policy and procedure template library
- System-generated risk ratings and remediation recommendations
- Customizable report of findings
- Product usability support provided by your guide
Validated Assessment
Remote and/or On-Site Assessor-Managed Assessment Utilizing HIPAA One
Our Validated PBRA Includes:
- Assessment readiness support provided by your assigned Assessor
- System workflow guides you through the assessment
- Access to policy and procedure template library
- Risk assessment validated by your Assessor(s)
- Remediation recommendations reviewed and approved by your Assessor(s)
- Assessor signs off on report of findings
- Technical and executive level ROF presentations
- Physical walk-through guidance (on-site)
Every Privacy & Breach Risk Assessment incorporates OCR Audit Protocol, HIPAA state specific regulations, 42 CFR Part 2 (SAMHSA) and maps findings to the NIST Privacy Framework
Why Industry Experts Choose HIPPA One®
Get a HIPAA One Demo
Additional Resources

Blog

Cybersecurity Checklist

